Connecting through SSH
Querious can utilitize SSH to create secure encrypted connections to remote servers.
NOTE: You can use the SSL and SSH security options in combination by simply turning both options. This will use an SSH tunnel to the remote SSH Host, and then from that machine connect through an SSL-secured socket to the MySQL Host machine.
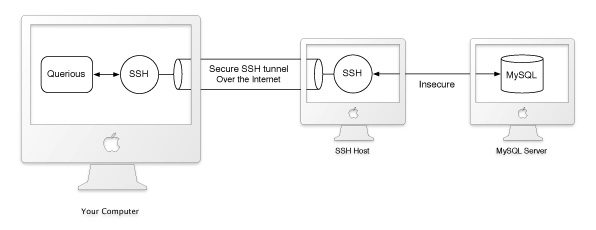
When using SSH, all communication with the MySQL server is forwarded through a secure tunnel created by SSH. See the diagram above for an illustration of this process. The local SSH instance creates a secure connection to SSH on a remote machine Querious calls the “SSH Host”. The local SSH instance listens to all traffic on a local port (“Tunnel Port”). The local SSH instance forwards all traffic coming into this local port, over the secure tunnel to the SSH Host, which then sends it over an insecure connection the destionation “Host” on the given “Port”.
Settings
The SSH Host and destination Host may actually be the same machine. In such cases, the “Host” would simply be “127.0.0.1” or “localhost”.
If for some reason you need to customize the tunnel creation, you can create an SSH tunnel using the command line instead of Querious.
Key-based Authentication
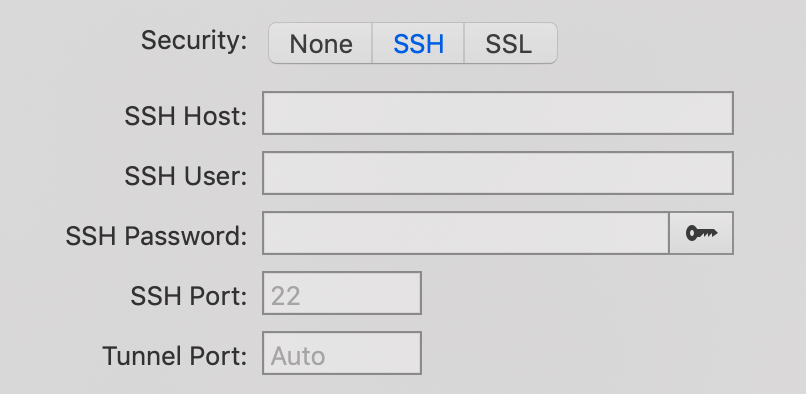
To use a private/public key pair to authenticate with SSH rather than a password, click on the key button at the end of the SSH Password field and select the public key.
If your private/public key pair is already registered with ssh-agent, or is one of the standard key names (id_rsa, id_dsa, etc) you may not need to select the key at all.
To create an SSH tunnel without Querious:
-
Open Terminal.app, and enter:
ssh -N username@serveraddress -L 8888:127.0.0.1:3306- “username” should be the remote username used to create an SSH connection at the internet address given by “serveraddress”.
- 8888 is simply any local unused port number.
- 3306 is the remote port for the database service (3306 is the default port for MySQL). You can change these settings as needed.
- After pressing return and entering in your SSH password, you can then use Querious to connect to the remote server.
- Open Querious and connect to the remote server by entering “127.0.0.1” into the Host field, and “8888” into the Port field. When you connect, all traffic sent to port 8888 of 127.0.0.1 will be encrypted and forwarded to port 3306 of the “serverAddress” machine specified in the SSH connection.
